Infrastructure as Code (IaC) is a method for defining and deploying IT infrastructure using a descriptive model and DevOps methodology. IaC offers benefits such as reproducibility, scalability, traceability and security of environments.
However, IaC also presents challenges related to complexity, change management and cloud costs. To address these challenges, there are tools available to improve the quality and efficiency of IaC. Among these tools, we can distinguish between SAST (Static Application Security Testing) tools and FinOps tools.
SAST tools are solutions that analyze the source code of applications to detect potential vulnerabilities before deployment. This helps to strengthen the security of applications and prevent vulnerabilities or attacks. SAST tools applied to Infrastructure as Code work by scanning your IaC code and comparing the defined configurations with a library of rules for each supported provider, which can be enhanced with customizable rules. These tools can detect configuration errors that may lead to security or compliance issues, and are easily integrated into CI/CD pipelines. Among the most used tools, we can find tfsec or checkov.
Use Case 1: you want to verify that your Terraform infrastructure followssecurity best practices, for example that your S3 buckets are encrypted or that your security groups are not too permissive. You can use tfsec or checkov to scan your Terraform code and get a report with detected violations and recommendations for fixing them.
Use Case 2: you want to enforce a policy as code (PaC) on your IaC infrastructure, for example that your cloud resources comply with PCI-DSS or CIS Benchmarks. You can use tfsec or checkov to define your own rules or use the default ones provided and scan your IaC code to verify that it complies with your policy.
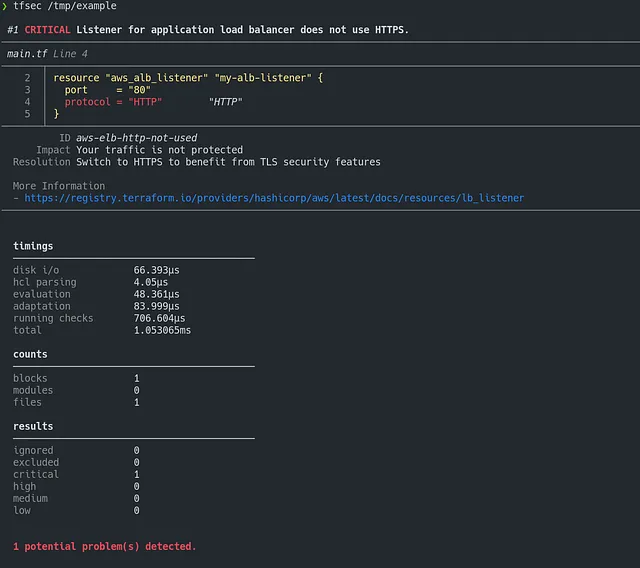
To test tfsec: https://killercoda.com/wescale/scenario/tfsec-basic
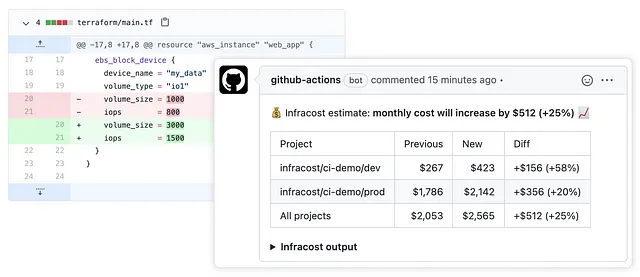
FinOps tools aim to optimize cloud-related costs by involving all stakeholders: finance, operations and governance. They help to better understand the use of cloud resources and reduce unnecessary or unplanned expenses. FinOps tools applied to IaC allow to calculate the estimated cost of resources before their deployment based on provider prices. These tools integrate with DevOps workflows and allow you to establish policies and safeguards to control your infrastructure costs and budget.
Use case: you want to know the financial impact of your infrastructure changes before they are applied to the cloud, for example how much it will cost you to add or remove an EC2 instance or an AKS cluster. To do this, infracost will generate a Terraform plan with the cost associated with each modified or added resource.
These tools can help to get the most out of IaC, but they are not a miracle solution. They require a good knowledge of the code and cloud resources used, as well as a good prioritization of remediation actions: indeed, it is not uncommon for a remediation proposed by tfsec to generate additional costs for example.
It is also important to be aware of the limitations and biases of these tools, which cannot cover all cases or guarantee absolute security or savings. It is therefore important to use them with discernment and to complement them with other practices such as monitoring, testing or auditing.
Sources :
- https://www.mediaglasses.blog/2021/08/24/tracking-costs-in-terraform-using-infracost/
- https://github.com/bridgecrewio/checkov
- https://learn.microsoft.com/en-us/azure/developer/terraform/best-practices-integration-testing
- https://github.com/aquasecurity/tfsec
- https://www.checkov.io/
- https://www.linkedin.com/pulse/using-checkov-policy-code-james-skliros
- https://www.infracost.io/
- https://lia.mg/posts/tfsec-and-opa-rego/